If you want to deploy a system in a federal environment or deliver software to a U.S. government agency, you need more than technical features or compliance paperwork.
You need an Authority to Operate (ATO).
Getting an ATO is one of the most critical and often misunderstood parts of working with the federal government. It’s not just a box to check. It’s a formal declaration that your system is secure enough to operate in a government environment.
In this article, we’ll walk through the complete ATO process, explain what’s required, and help you understand what it takes to reach the finish line without burning time or budget.
What Is an ATO?
An Authority to Operate (ATO) is formal approval from a government agency that allows your system, application, or product to operate in their environment. It confirms that the system meets federal cybersecurity standards and has an acceptable level of risk.
Without an ATO, you can’t deploy your technology into production for federal use. Period.
Who Needs an ATO?
You may need an ATO if:
- You’re building a cloud or SaaS product for a federal agency.
- You’re deploying a tool into a government network.
- You’re processing Controlled Unclassified Information (CUI).
- You’re part of a contract requiring system authorization.
Common frameworks that drive the ATO process include NIST SP 800-53, FedRAMP, and DoD RMF (Risk Management Framework).
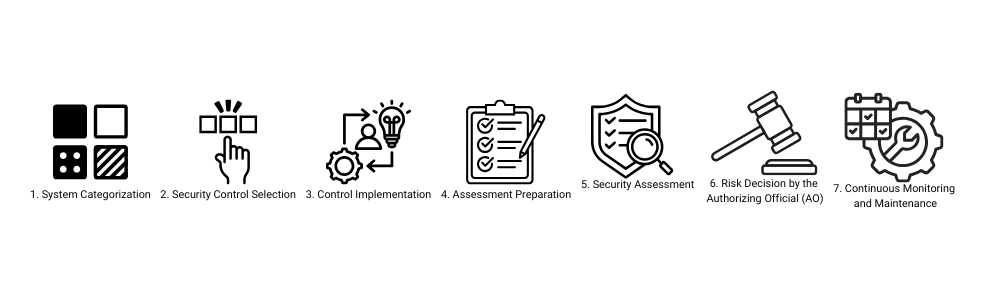
The 7 Stages of the ATO Process
1. System Categorization
This step involves defining the security impact level of your system based on the Federal Information Processing Standard (FIPS) 199. You’ll assess the potential impact of confidentiality, integrity, and availability losses as low, moderate, or high.
This decision determines the controls and documentation required later in the process.
2. Security Control Selection
Based on the categorization, you’ll select a set of security controls from NIST SP 800-53 (or the relevant framework). These controls cover access management, encryption, auditing, and incident response.
You’ll map which controls are relevant and determine how they will be implemented.
3. Control Implementation
This is where you apply the selected controls to your system. It includes:
- Technical configuration
- Policy enforcement
- Security monitoring setup
- Staff training
You must also document everything. This becomes part of your System Security Plan (SSP).
4. Assessment Preparation
Before an official assessment, most organizations conduct a pre-assessment or gap analysis. This step helps identify weaknesses or missing documentation before the real audit begins.
You’ll also finalize your:
- System Security Plan (SSP)
- Plan of Action and Milestones (POA&M)
- Risk Assessment Report (RAR)
- Security Assessment Plan (SAP)
5. Security Assessment
A third-party assessor or internal audit team will evaluate your implementation, documentation, and system readiness.
This stage includes:
- Interviews
- Document reviews
- Technical validation
- Penetration testing (if required)
The result is a Security Assessment Report (SAR) that outlines findings and recommendations.
6. Risk Decision by the Authorizing Official (AO)
The completed package is submitted to the agency’s Authorizing Official, who reviews the system’s posture and residual risk. They decide whether to:
- Grant an ATO (Authority to Operate)
- Grant an IATO (Interim ATO with conditions)
- Issue a Denial if risks are too high
The AO considers security, mission impact, and business needs.
7. Continuous Monitoring and Maintenance
An ATO isn’t permanent. Once granted, you must continuously monitor the system and report on key indicators. That includes:
- Monthly or quarterly system scans
- Incident response tracking
- Annual control reviews
- POA&M updates for unresolved risks
You’ll also need to maintain your documentation for audits, recertification, or contract renewals.
How Long Does the ATO Process Take?
It depends on your system’s complexity and how prepared you are. Here’s a rough timeline:
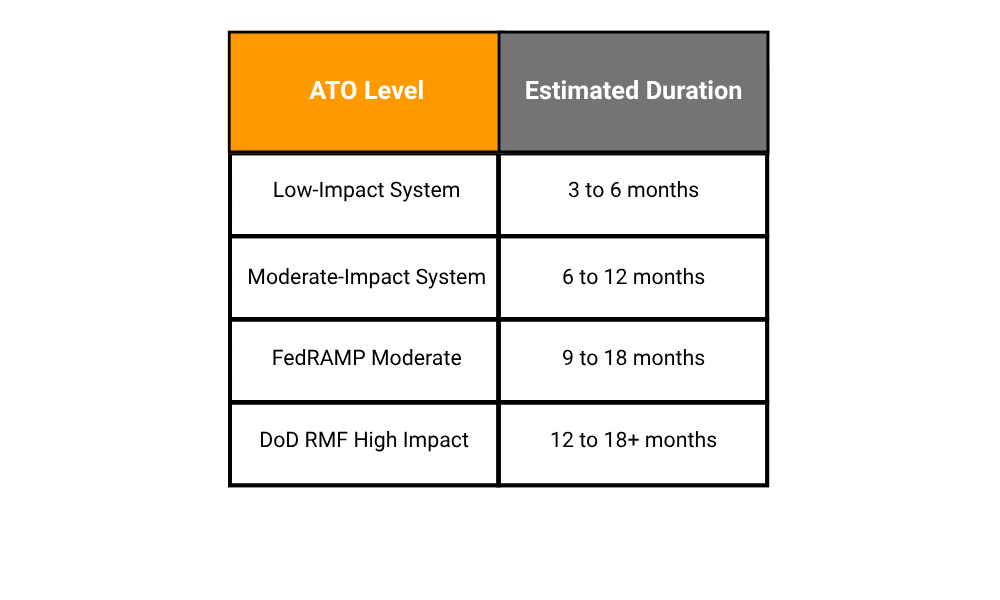
Trying to rush it without preparation often leads to delays and rework.
Common Pitfalls
- Missing documentation (especially SSPs and POA&Ms)
- Unclear ownership of the ATO process
- Assuming the process is purely technical
- Treating security as an afterthought
- Underestimating the timeline and scope
Avoiding these pitfalls starts with involving the right stakeholders early and making cybersecurity part of your core system design, not a bolt-on.
Final Thought
The ATO process is complex. But it’s also predictable when you know what to expect. With the right approach, clear documentation, and early planning, your team can move through the steps confidently and avoid unnecessary delays.
At Black Rock Engineering & Technology, we help contractors and technology providers navigate the ATO process with speed, clarity, and compliance.
Need help building a roadmap or preparing for authorization? Schedule a call and we’ll walk you through it step-by-step.

