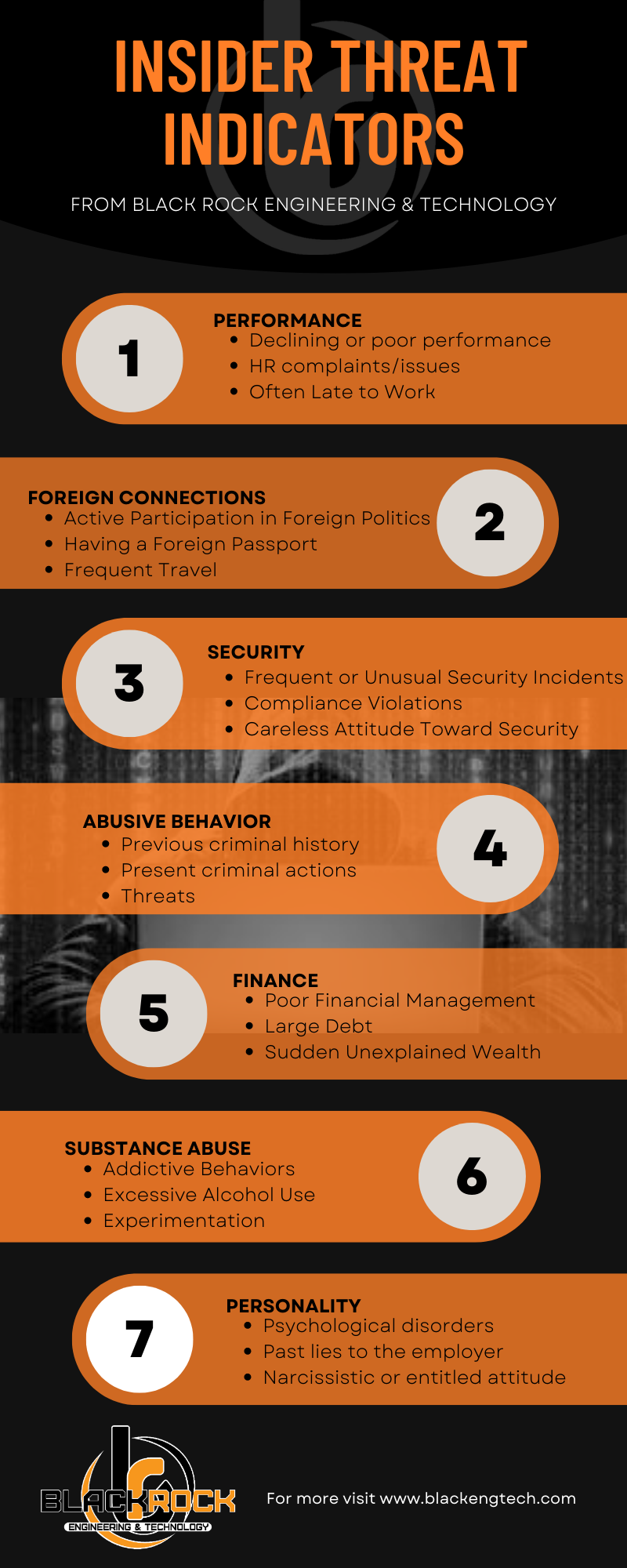
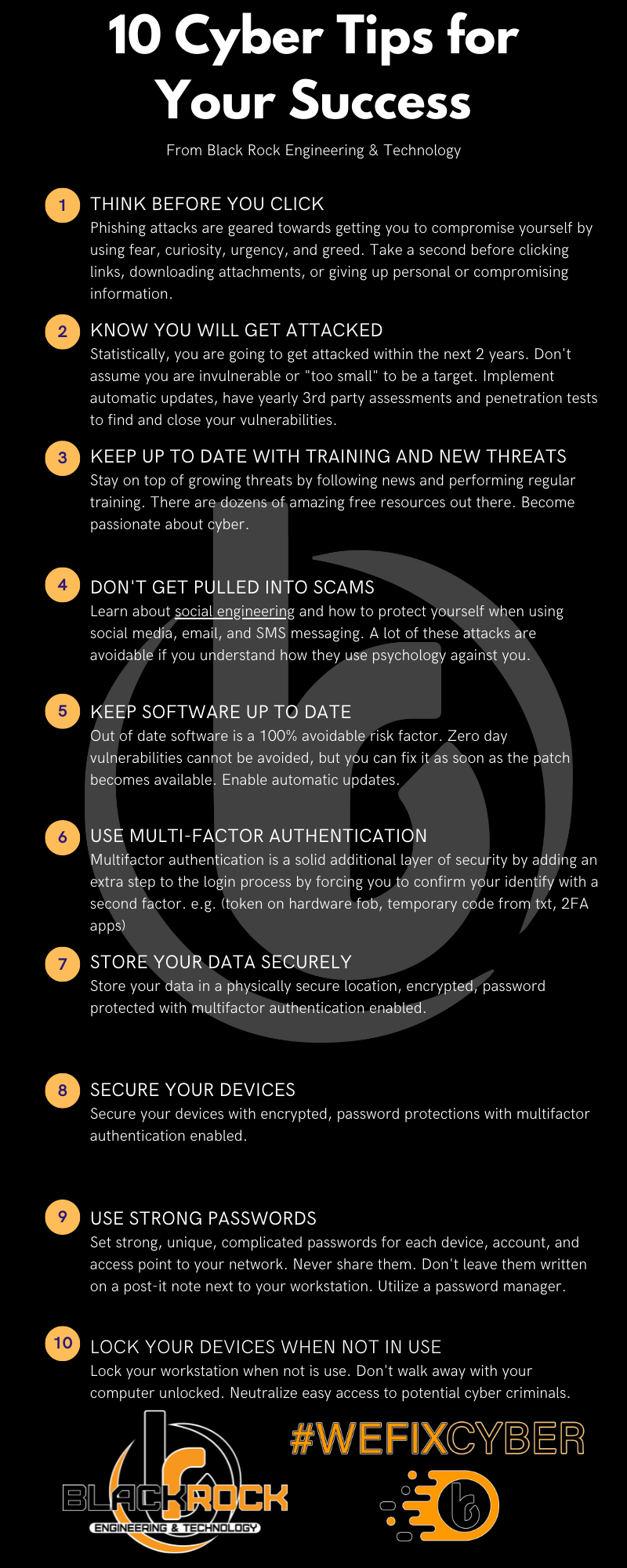
If a picture is worth a thousand words Black Rock has written you a book! We utilize our infographics to communicate key cybersecurity concepts and leverage them to improve our end-user training.
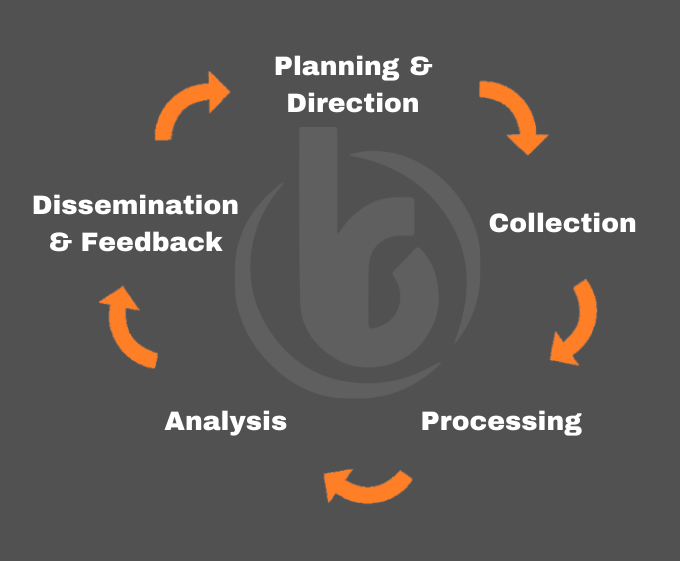
Planning and direction:
Set the range and objectives for intelligence roles and processes.
Collection:
Deploy data gathering techniques and resources.
Analysis:
Translate unprocessed intelligence into meaningful actors, events, and attributes.
Production:
Assess the significance and severity of the translated intelligence based on operational context.
Dissemination and feedback:
Submit the finished intelligence report, remembering importance and confidentiality.
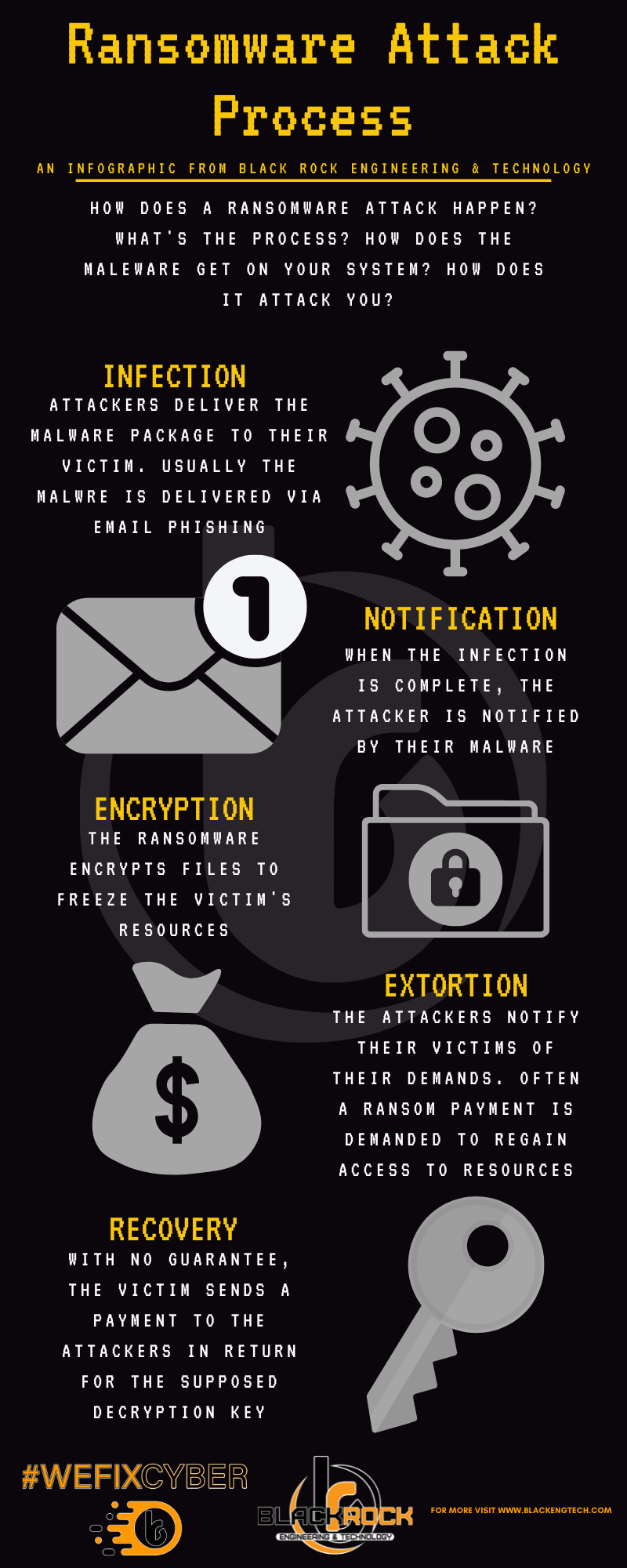

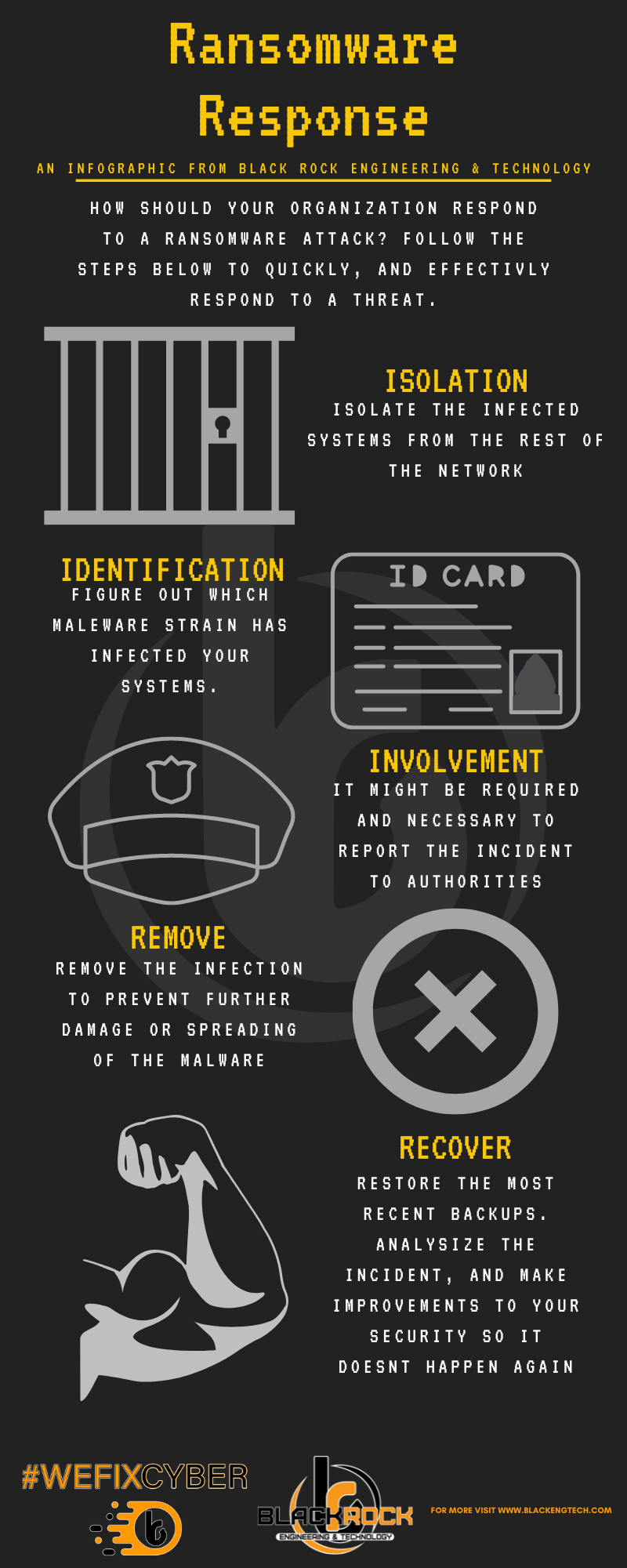

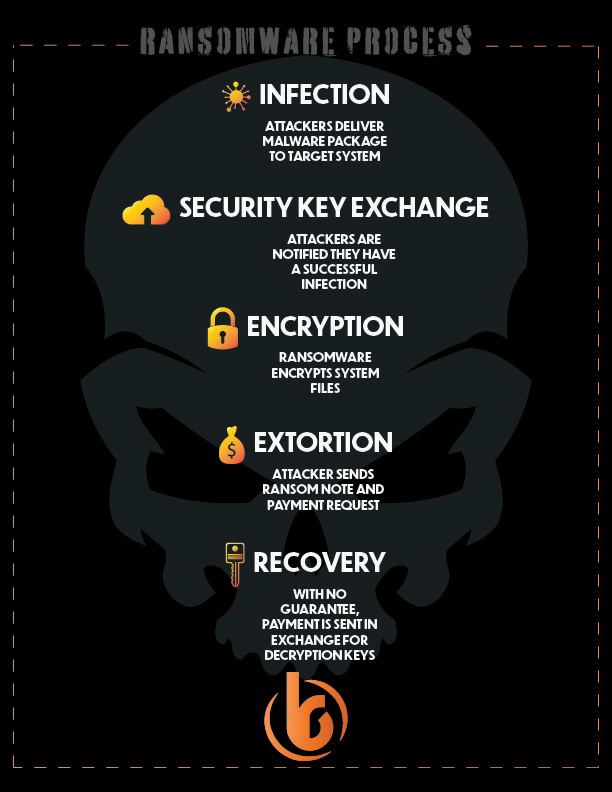
Black Rock's Ransomware Series can be utilized for the "at home" and corporate end user. By visualizing the ransomware process and protection tips we hope to make it easier for anyone to understand the ever-present threat of ransomware, and how to protect themselves and their organizations.

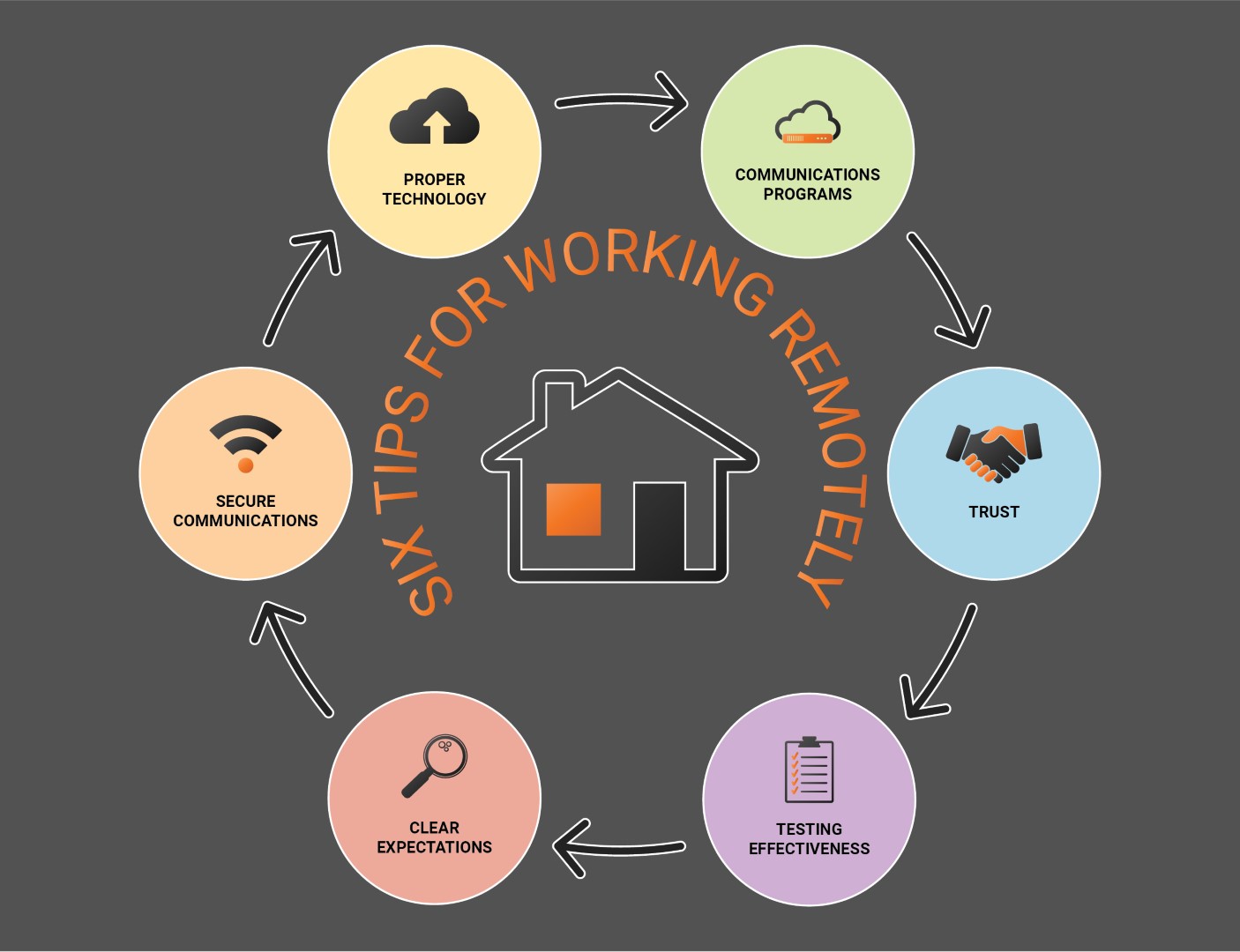
Proper technology: Computer, secure email, phone conferencing, secure access to internal networks.
Secure Communications: A Trusted virtual private network (VPN) on your mobile device or laptop. Updated secure Wi-Fi protocols.
Communications programs: Stay in touch with employees who work from home via Teams, Slack, and other messaging services. Clear, secure communication ensures your team is connected and moving forward.
Clear expectations: Create a work from home policy including instructions for an employee’s daily work schedule, description of a dedicated workspace, directions for reporting damage to company equipment, and how to protect company data.
Testing Effectiveness: If you are setting up a work from home policy, make sure to monitor for compliance with security standards and potential improvements.
Trusting your employees: Trust in your employees to get their jobs done when they are not working onsite. Give them clear direction and help them secure their workspace. Then trust them to figure out the rest. They aren’t in the office anymore so they shouldn’t feel like you’re right behind them.
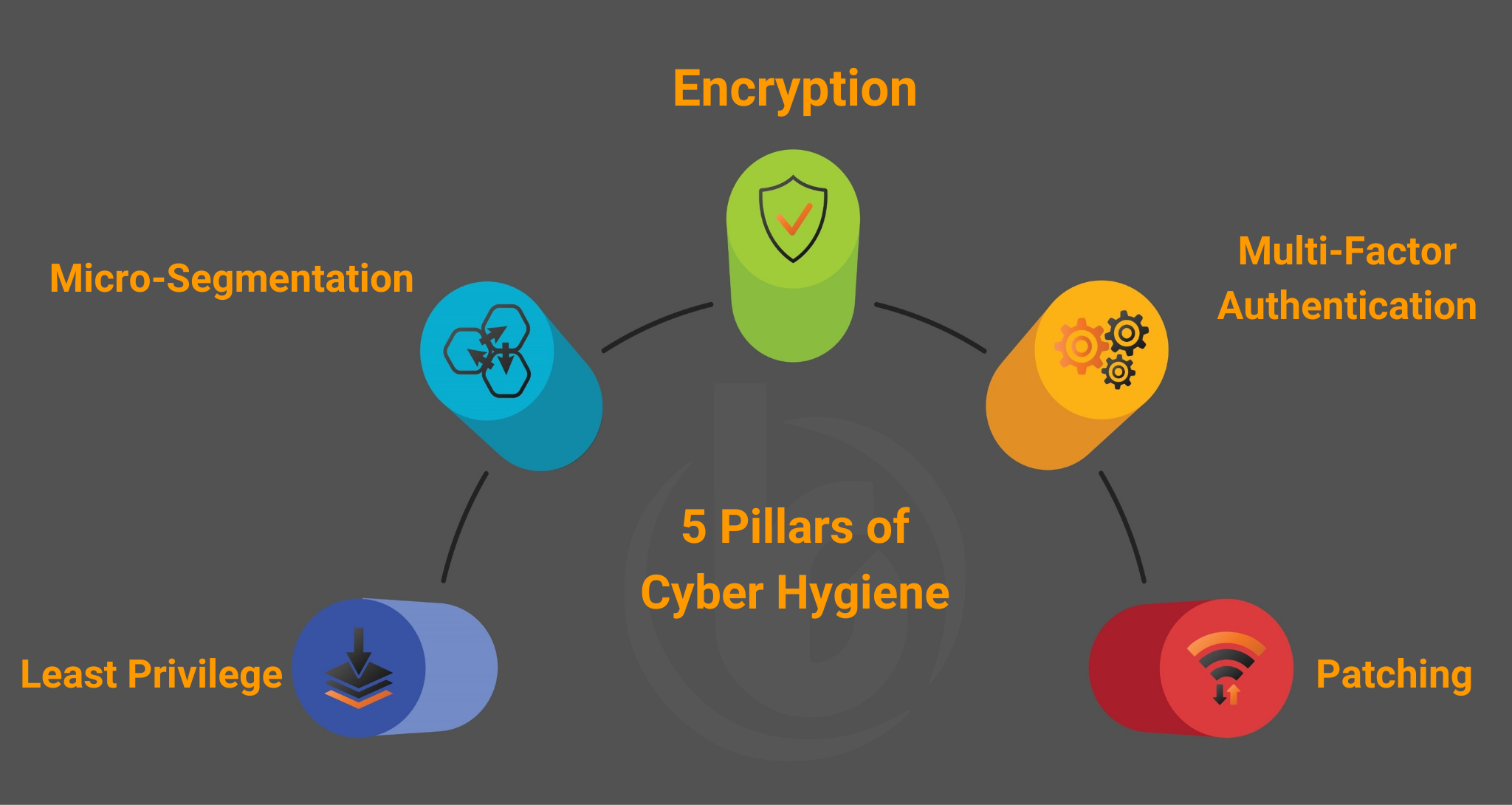
Least Privilege: Following least privilege means you ensure your users have access to resources they need to do their work, and nothing more. IT doesn’t need access to payroll, right? So why give them access?
Micro-Segmentation: Micro-segmentation is when you logically divide the network resources into subnets. The accounting network doesn’t need to talk to the C-suit network. Similar to least privilege it prevents access to communications that are not required to do their work.
Encryption: End to end encryption. Encrypt data going across your network. Encrypt data on the workstations. Encrypt data going out to the internet. To ensure data that leaks out is not usable, encrypt it.
Multi-Factor Authentication: When you force your end users to use multi-factor authentication is provides remediation in the authentication process. Meaning, if a user’s name and password is compromised, but the user still has their phone for SMS multifactor authentication the attacker will have a much harder time getting access.
Patching: Make sure your operating systems, software, and equipment firmware, is patched and up to date. Enable automatic updates for patches. If your firmware is no longer receiving updates, consider removing that device from the network or replacing to a newer model.
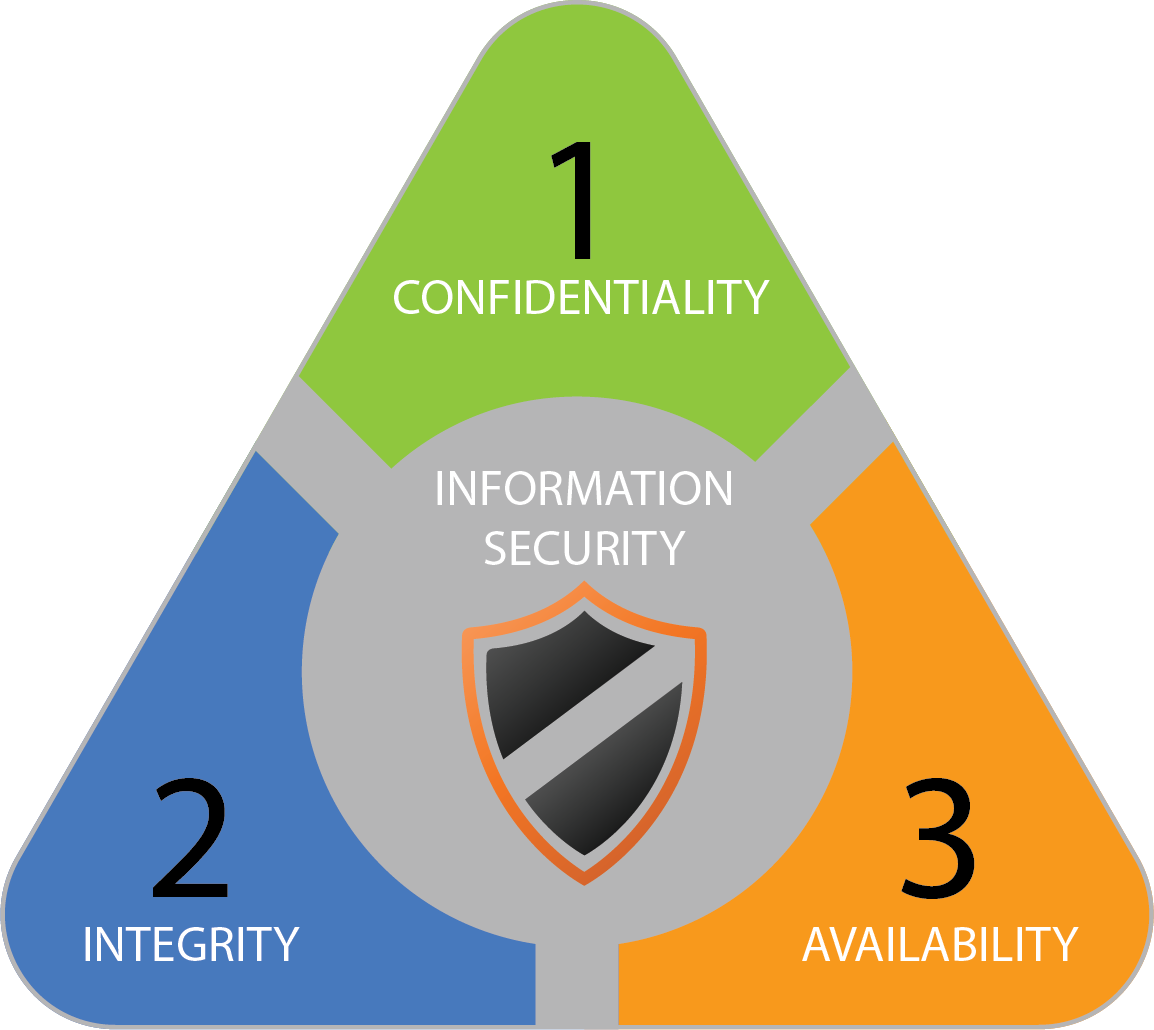
CONFIDENTIALITY: Protecting your sensitive, private information from unauthorized access.
INTEGRITY: Protecting your data from deletion or modification from any unauthorized party. Also, ensuring that when an authorized person makes a change that should not have been made, it can be reversed.
AVAILABILITY: We want our data when we need it. We don't want it available to any unauthorized persons.
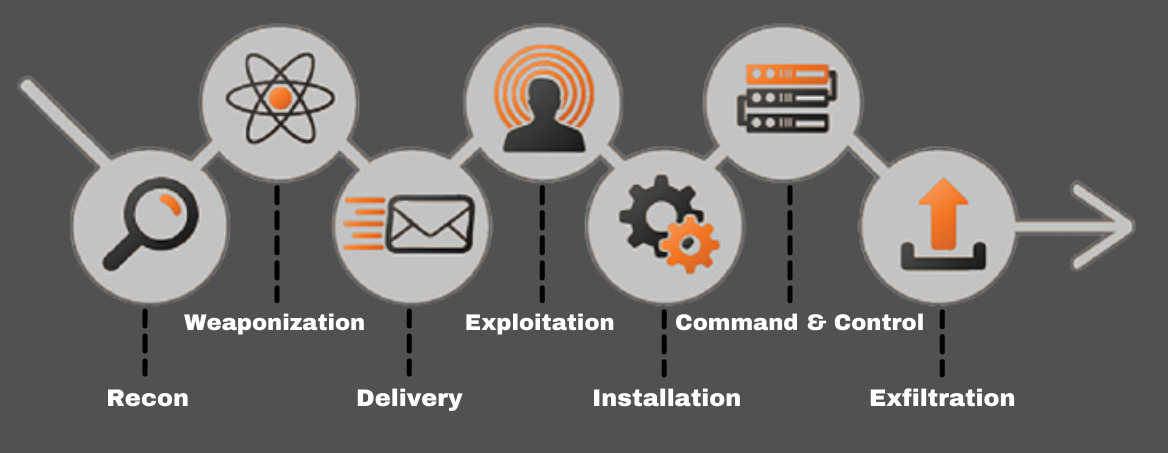
Recon: In this step, the attacker / intruder chooses their target. Then they conduct an in-depth research on this target to identify its vulnerabilities that can be exploited.
Weaponization: In this step, the intruder creates a malware weapon like a virus, worm or such in order to exploit the vulnerabilities of the target. Depending on the target and the purpose of the attacker, this malware can exploit new, undetected vulnerabilities (also known as the zero-day exploits) or it can focus on a combination of different vulnerabilities.
Delivery: This step involves transmitting the weapon to the target. The intruder / attacker can employ different methods like USB drives, e-mail attachments and websites for this purpose.
Exploitation: In this step, the malware starts the action. The program code of the malware is triggered to exploit the target’s vulnerability/vulnerabilities.
Installation: In this step, the malware installs an access point for the intruder / attacker. This access point is also known as the backdoor.
Command and Control: The malware gives the intruder / attacker access in the network/system.
Exfiltration: Once the attacker / intruder gains persistent access, they finally take action to fulfill their purpose, such as encryption for ransom, data exfiltration or even data destruction.