Keeping legacy systems in place may seem like a cost-saving measure, but in regulated industries, such as defense contracting, outdated technology can pose a direct threat to compliance.
Many organizations don’t realize just how much risk these old systems introduce until it’s too late.

Risk 1: Unsupported Software and Security Gaps
When vendors stop supporting a product, you stop receiving security patches.
This means any vulnerability discovered after that date remains unpatched, making it a clear compliance violation under most frameworks, including CMMC and NIST SP 800-171.
For example, A legacy server running an end-of-life operating system cannot meet current security standards without incurring costly, custom mitigation measures.
Risk 2: Inability to Implement Required Controls
Compliance frameworks often require specific security controls, such as MFA, encryption, and detailed logging.
Many legacy systems either can’t support these controls or require complex, unreliable workarounds.
If you can’t implement a mandated control, you risk:
- Failed audits
- POA&Ms that delay certification
- Contract loss or penalties
Risk 3: Integration Blind Spots
Modern compliance relies on visibility into data flow.
Legacy systems often fail to integrate well with newer monitoring and reporting tools, creating blind spots that auditors will likely flag.
Without seamless integration, it’s harder to prove compliance in real time.
Risk 4: Higher Likelihood of Human Error
Legacy systems typically require more manual processes for updates, backups, and reporting.
The more manual work involved, the greater the chance of missed steps and inaccurate records, both of which auditors are likely to notice.
Risk 5: Escalating Maintenance Costs
It’s not just a compliance risk; it’s a financial risk.
As hardware ages and software becomes more difficult to maintain, the cost of keeping legacy systems running can quickly exceed the cost of modernization.
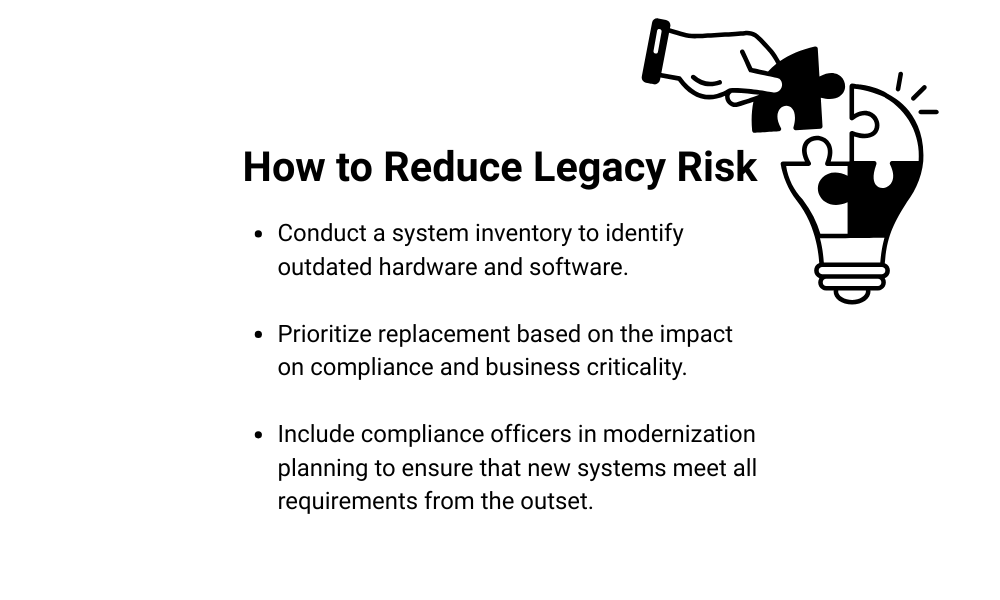
Why This Matters
Legacy systems can quietly erode your compliance posture until an audit or security incident forces you to take action.
By identifying and replacing them proactively, you can protect both your contracts and your reputation.
Take the First Step
Our Tech Modernization Checklist includes a comprehensive system assessment section designed to identify legacy risks before they lead to compliance failures.
See where outdated technology may be putting your organization at risk.
